KAUST Information Security Department
Password Reset – Phishing Campaign: Winners and Information
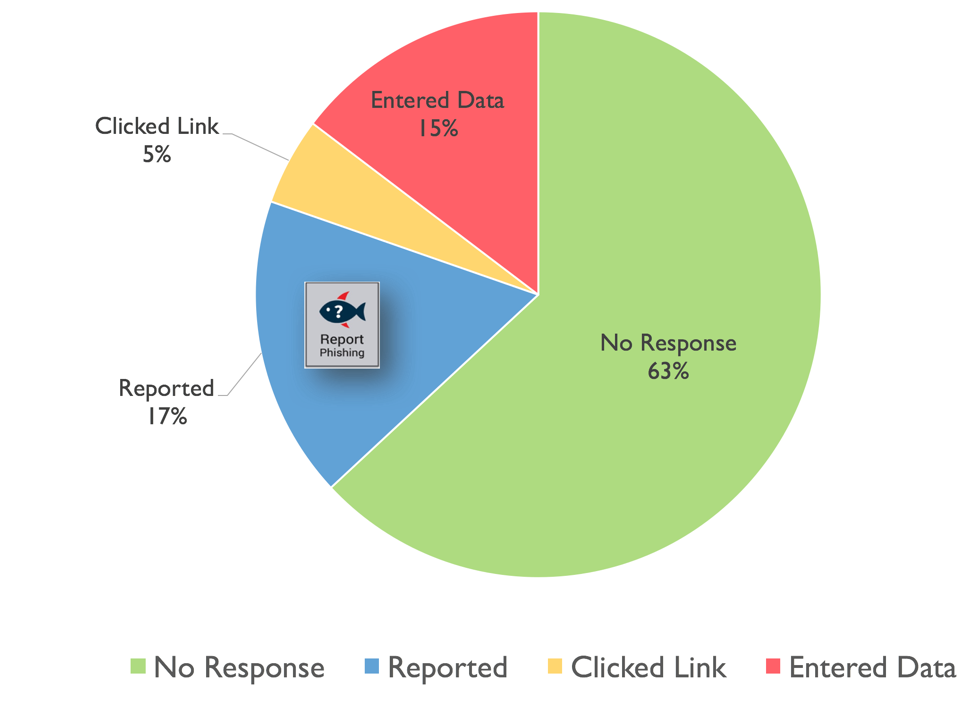
The KAUST Information Security Department has run a phishing simulation pretending to be a hacker telling you that your password needs to be reset due to compromise. This specific scenario was designed to be very similar to actual phishing emails that KAUST has been targeted with recently. The hackers in this case have used our own Webmail landing page to lure people into entering their passwords. This scenario has proven to us that our users are indeed more likely to supply information to a familiar looking website. The elements of this phish were:
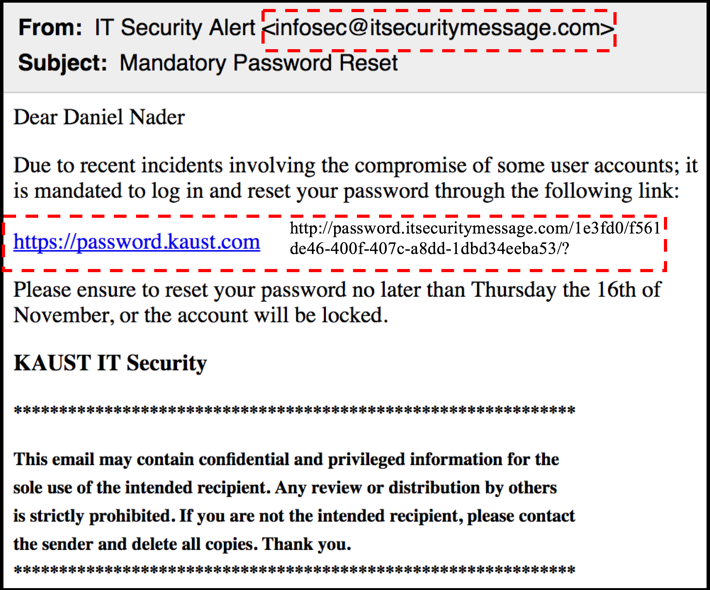
- Sent from a generic but familiar sender “IT Security Alerts”, however if you do check the email address it is not a KAUST email.
- Link uses kaust.com. This is not a registered KAUST domain. We use kaust.edu.sa.
- Hovering over the link will expand a tooltip showing you the actual site behind the hyperlink. Make sure it points to a known domain that makes sense for the subject of the email.
- The landing page of the link is an exact copy of the KAUST webmail site. Copying HTML and graphics is extremely easy. Make sure to check the address bar before supplying any information.
- The signature is KAUST IT Security, this is text, and anyone can type in text.
- The email has a “disclaimer” in it, to make it appear more legitimate.
- The email preys on the victim’s emotions; their sense of duty, their fear of being compromised, and urgency by giving a deadline for action.
These simple checks before you take any action on an email can help you avoid falling victim to a phish. It may seem difficult and redundant to do for every email, but it does become a habit after some time.
PHISHING F.A.Q:
What is phishing?
Sending emails purporting to be from familiar sources in order to build trust and induce individuals to reveal personal information, such as passwords or credit card numbers. This can also apply to chat messages or SMS.
What is KAUST doing about phishing?
We do have technical controls and response teams that are working around the clock, those cover the majority of harmful behaviors programmed into malicious codes. However, hackers with the intent of causing harm are always trying to stay one step ahead by evading these controls with what appears to be a harmless email. It then becomes the job of the user to be vigilant and identify such emails.
The KAUST Information Security Department will from time to time conduct phishing simulations by sending out similar emails to train individuals on identifying such emails and stay vigilant and aware. The scope of these simulations is everyone with a KAUST account.
How do I react when I suspect an email to be a phishing attempt?
Report it! Whether it is a real phish from a hacker, a simulation by Information Security, or an email that just does not feel right; you should always report it. This has immensely helped us in the past in thwarting off hacking attempts.
Any user using Microsoft Outlook on Mac or Windows will have a ‘Report a Phish’ button. In the event you do not use Microsoft Outlook, you can forward the email to phishreporter@kaust.edu.sa.
Windows Users: The button is found in the ribbon on the top right of the screen. Highlight the email you want to report and then click the button.
Mac Users: The button is found in the dock on the bottom left of the screen (This can be customized by users). Highlight the email you want to report and then click the button.
If you do not see the button or cannot find it; contact the IT HelpDesk and they can assist you.
Sometimes I see announcements (like this one) that have links leading to sites other than KAUST’s, what should I do?
KAUST Announcements and Lens Posts use a system called E2MA, links will direct to the tool first for statistical purposes and then take you to the content you want to see. Wufoo, Form Stack, and Survey Monkey are some of the other tools used for surveys and online forms and can all be considered safe. Our best advice is to always check the sender and if in doubt, contact the sender or report it to us for analysis.
How is phishing different from spam?
Spam is the annoying and sometimes meaningless email junk that comes into our inboxes. It does not ask for your personal or confidential information and is frequently advertisements sent in bulk to many users. Phishing on the other hand asks you to click on a link, provide your username/password, banking information, or sensitive information. Spear-phishing is when it becomes a targeted email sent to a specific user or set of users.
Our Winners:
Every simulation conducted has a drawing for prizes to reward our vigilant users who are the fastest to report it. We rely on our users to be aware and report emails to us that may bypass our controls. This round’s winners are:
- Susan P. Mulholland
- Ammar M. Abdali
- Arif S. Mohammed
Additional Questions?
If you would like additional information or have any questions you can always reach out to the KAUST Information Security Department at: askinfosec@kaust.edu.sa.

